The best security for the remote management unit in your server such as IPMI/KVM is to have local IP. All IPMI/KVM IP should be switched to a separated switch and a local sub-network used for the LAN Settings. So to be able to connect to the IPMI/KVM module you need a VPN connection to gain access to the local sub-network used for your servers’ management modules. However, sometimes the VPN cannot be used or it just happened the server is down, or you are at a place restricting unknown ports (or ports above 1024), which your VPN uses (that’s why the VPN server should use only one port from the most popular – 80, 443, but that’s a thing for another howto…) and so on. So you end with no ability to connect to the VPN server or you think you do not need at all a VPN server, because you always could use
openssh
to do the trick of tunneling ports from your computer to the IPMI/KVM module of your server through a server, which has an access to the local sub-network of the IPMI/KVM modules.
So here is what you need to get to the remote management of your server just using ssh for tunneling:
STEP 1) A server, which has access to the IP network of the IPMI/KVM modules.
Let’s say you set to all your servers’ IPMI/KVM modules IPs from network 192.168.7.0/24, so your server must have an IP from 192.168.7.0/24, for example 192.168.7.1, add it as an alias or to a dedicated LAN connected to the switch, in which of all your IPMI/KVM modules are plugged in. This server will be used as a transfer point to a selected IPMI/KVM IP.
STEP 2) Tunnel local selected ports using ssh to the server from STEP 1)
Use this command:
ssh -N -L 127.0.0.1:80:[IPMI-IP]:80 -L 127.0.0.1:443:[IPMI-IP]:443 -L 127.0.0.1:5900:[IPMI-IP]:5900 -L 127.0.0.1:623:[IPMI-IP]:623 root@[SERVER-IP]
For example using 192.168.7.150 for an IPMI/KVM IP:
[root@srv0 ~]# ssh -N -L 127.0.0.1:80:192.168.7.150:80 -L 127.0.0.1:443:192.168.7.150:443 -L 127.0.0.1:5900:192.168.7.150:5900 -L 127.0.0.1:623:192.168.7.150:623 root@example-server.com
With the above command you can use the web interface (https://127.0.0.1/, you could replace 127.0.0.1 with a local IP or a local IP alias of your machine), the java web start “Console Redirection” (the KVM – Keyboard, Video and Mouse) and you can mount Virtual Media from your computer to your server’s virtual CD/DVD device. Unfortunately to use properly the Virtual CD/DVD you must tunnel the UDP on port 623 (not only TCP 623), which is a little bit tricky. To tunnel the UDP packets
socat – Multipurpose relay (SOcket CAT)
program must be used.
STEP 3) Tunnel local selected ports using ssh to the server from STEP 1) and UDP port using socat
[root@srv0 ~]# socat -T15 udp4-recvfrom:623,reuseaddr,fork tcp:localhost:8000 [root@srv0 ~]# ssh -L8000:localhost:8000 -L 127.0.0.1:80:192.168.7.150:80 -L 127.0.0.1:443:192.168.7.150:443 -L 127.0.0.1:5900:192.168.7.150:5900 -L 127.0.0.1:623:192.168.7.150:623 root@example-server.com socat tcp4-listen:8000,reuseaddr,fork UDP:192.168.7.150:623
This will start a UDP listening socket on localhost port 8000. Every packet will be relayed using TCP to localhost 8000, which will be tunneled using ssh command to the remote server, where there is a started another socat listening TCP socket on port 8000, which will relay every packet to the UDP port 623 of IP 192.168.7.150. Replace the IP 192.168.7.150 with your IPMI/KVM IP.
* Here are the required ports for SUPERMICRO IPMI functionality in X9 and X10 motherboards
-
X9-motherboards, the ports are
TCP Ports
HTTP: 80
HTTPS: 443
SSH: 22
WSMAN: 5985
Video: 5901
KVM: 5900
CD/USB: 5120
Floppy: 5123
Virtual Media: 623
SNMP: 161UDP ports:
IPMI: 623 -
For X10-motherboards, the ports are
TCP Ports
HTTP: 80
HTTPS: 443
SSH: 22
WSMAN: 5985
Video: 5901
KVM: 5900 , 3520
CD/USB: 5120
Floppy: 5123
Virtual Media: 623
SNMP: 161UDP ports:
IPMI: 623
You could add the required port to the ssh command above if you need it!
Virtual Device mounted successfully
Successful mount in Console Redirection with Virtual Media:
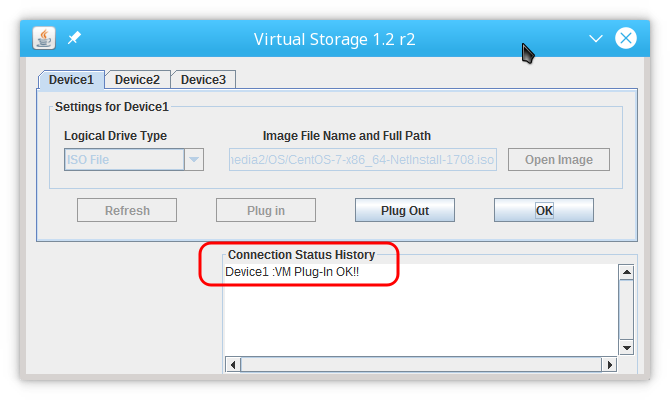
if you are logged in the server and mount an ISO with the Virtual Device you’ll probably have this in “dmesg”:
[46683751.661063] usb 2-1.3.2: new high-speed USB device number 8 using ehci-pci [46683751.795048] usb 2-1.3.2: New USB device found, idVendor=0ea0, idProduct=1111 [46683751.795051] usb 2-1.3.2: New USB device strings: Mfr=0, Product=0, SerialNumber=0 [46683751.795365] usb-storage 2-1.3.2:1.0: USB Mass Storage device detected [46683751.795553] scsi6 : usb-storage 2-1.3.2:1.0 [46683752.795730] scsi 6:0:0:0: CD-ROM ATEN Virtual CDROM YS0J PQ: 0 ANSI: 0 CCS [46683752.806839] sr0: scsi3-mmc drive: 40x/40x cd/rw xa/form2 cdda tray [46683752.806842] cdrom: Uniform CD-ROM driver Revision: 3.20 [46683752.806933] sr 6:0:0:0: Attached scsi CD-ROM sr0 [46683752.806971] sr 6:0:0:0: Attached scsi generic sg1 type 5

One thought on “Tunneling the IPMI/KVM ports over ssh (supermicro ipmi ports)”