Moving towards the firewalld software and especially the systemd some good old init scripts got missing! For example, one of those good scripts is the init script for iptables firewall, which allows saving iptables rules and during boot, it loads them again. With the init iptables script we have persistence of the iptables rules. Meanwhile, we can always call the init script with “save” argument to update the currently saved rules. Many different Linux distributions have this init script – “/etc/init.d/iptables”, but in systemd world, it has been removed and replaced with nothing (probably, because you are encouraged to use firewalld, which is not a bad thing!).
There are two packages “iptables-persistent” and “netfilter-persistent”, which work together to have iptables persistence over reboots. The rules are saved and restored automatically during system startup.
First, install “iptables-persistent” and “netfilter-persistent” with
sudo apt install netfilter-persistent iptables-persistent
During the iptables–persistent installation the setup asks the user to save the current iptables rules. Hit “Yes” if you want to save the current iptables rules, which will be automatically loaded the next time the system starts up.
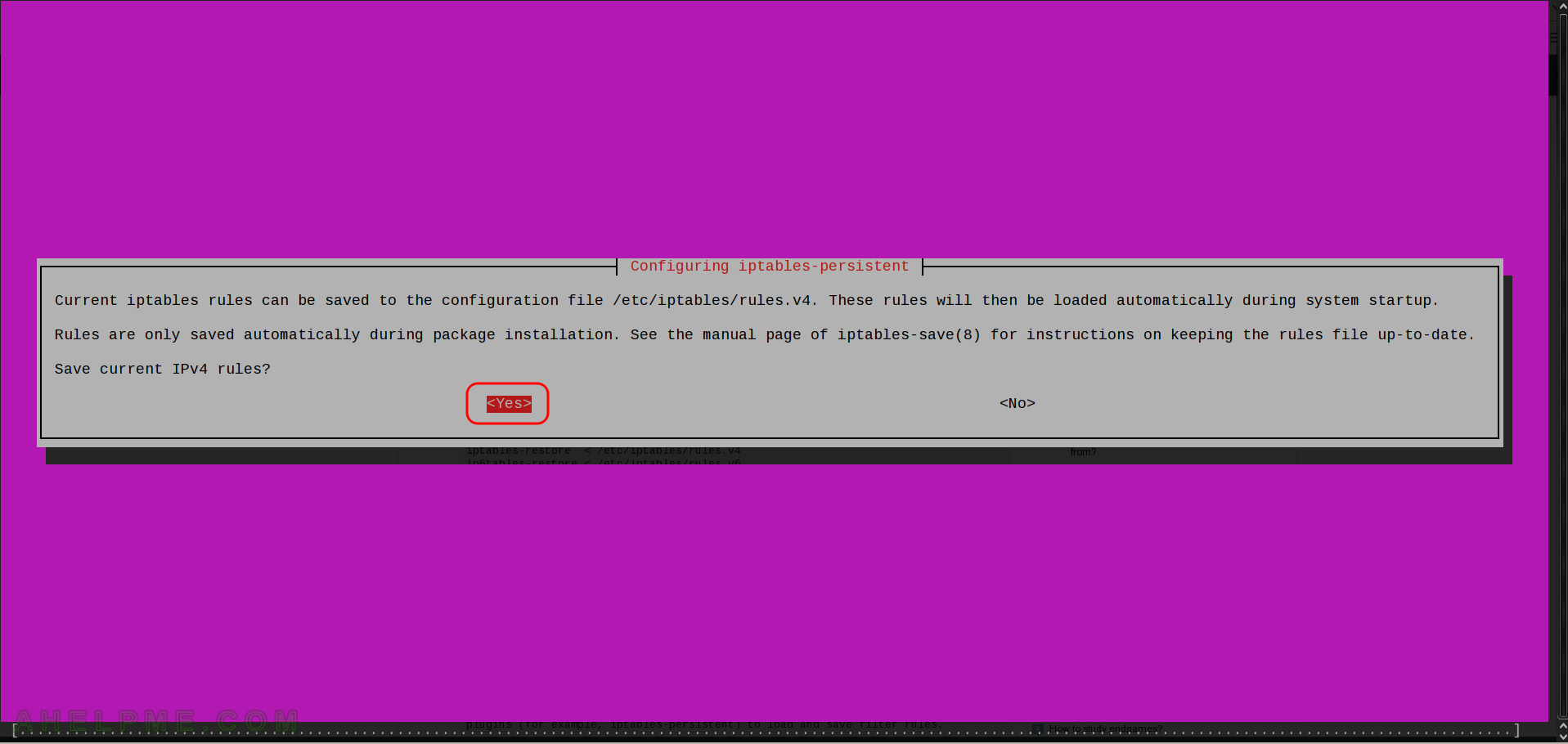
So it is safe to install it on a live system – the current iptables rules won’t be deleted.
Second, ensure the boot script to restore the iptables rules is enabled
sudo systemctl enable netfilter-persistent
Additional information
Saving the current state of the iptables rules:
myuser@myubuntupc:~$ sudo /usr/sbin/netfilter-persistent save run-parts: executing /usr/share/netfilter-persistent/plugins.d/15-ip4tables save run-parts: executing /usr/share/netfilter-persistent/plugins.d/25-ip6tables save
Restore the original state of the iptables rules:
sudo systemctl restart netfilter-persistent
And all commands you can do – start, stop, restart, reload, flush, save. You can use the script directly (it is not mandatory to use systemctl to restart, i.e. restore rules and etc.)
myuser@myubuntupc:~$ sudo /usr/sbin/netfilter-persistent Usage: /usr/sbin/netfilter-persistent (start|stop|restart|reload|flush|save)
The script netfilter-persistent executes 2 other scripts as plugins:
/usr/share/netfilter-persistent/plugins.d/15-ip4tables /usr/share/netfilter-persistent/plugins.d/25-ip6tables
The iptables rules are saved respectively in files
/etc/iptables/rules.v4 /etc/iptables/rules.v6
And you can always edit them manually or save/restore with iptables-save and iptables-restore redirecting the output to the above files.
It’s normal the state of the “active (exited)”. The service is “enabled” as you can see (by default the setup automatically enables the service on Ubuntu, but always check it to be sure, it’s the firewall!).
myuser@myubuntupc:~$ sudo systemctl status netfilter-persistent ● netfilter-persistent.service - netfilter persistent configuration Loaded: loaded (/lib/systemd/system/netfilter-persistent.service; enabled; vendor preset: enabled) Active: active (exited) since Thu 2019-01-17 20:44:08 EST; 14min ago Main PID: 666 (code=exited, status=0/SUCCESS) CGroup: /system.slice/netfilter-persistent.service Jan 17 20:44:08 myubuntupc systemd[1]: Starting netfilter persistent configuration... Jan 17 20:44:08 myubuntupc netfilter-persistent[666]: run-parts: executing /usr/share/netfilter-persistent/plugins.d/15-ip4tables start Jan 17 20:44:08 myubuntupc netfilter-persistent[666]: run-parts: executing /usr/share/netfilter-persistent/plugins.d/25-ip6tables start Jan 17 20:44:08 myubuntupc systemd[1]: Started netfilter persistent configuration.
You have same issue here as those about 1000 others who has been wrote same thing. Your heading is wrong. It should be “How to load iptables rules after reboots”.
_saving_ is still something one must do manually if followed this tips.